this will add all the [domain]'s subdomains in burp suite .*.domain.com$
Tips:
- Look for a company that suites with your interests or industry expertise.
- Check thier triager response as well as the reward offered for bugs.
- Read about other hackers' experiences and findings for that company if its a large company.
Paying attention to out of scope / exclusions list:
XSS, CSRF, Business Logic, Info Disclosure, Subdomain Takeovers
Automate your works:
If you write the same command (that is relative long) 2 or more times a day, then make a function in bashrc or make a script and move it to /usr/local/bin to call it from everywhere. This will save you time.
- Automate subdomain enumeration and discovery.
- Automate brute-forcing directories.
- Automate visualization of live subdomains.
- Automate everything that takes "long" time to do it manually so you can focus on something else while it is running.
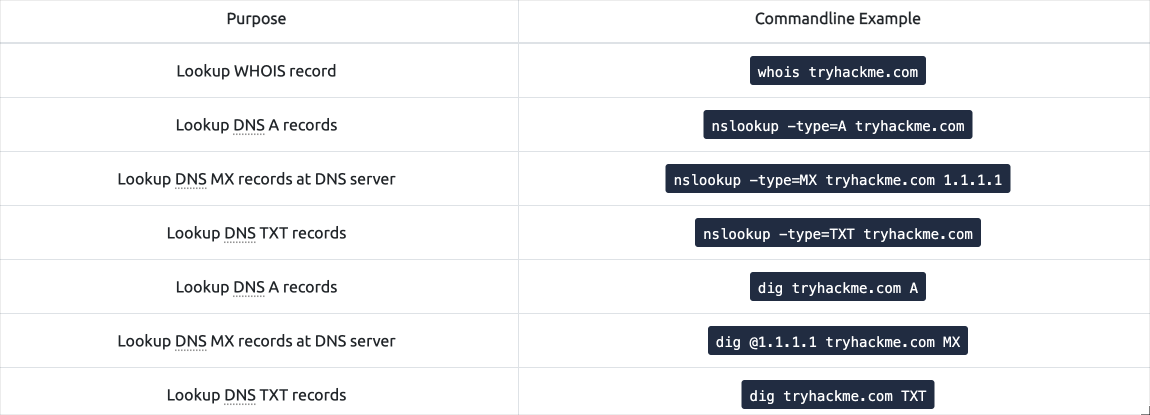
Scan:
- https://remonsec.com/posts/passive-recon-with-spyse-part-I/
- https://remonsec.com/posts/passive-recon-with-spyse-part-II/
- technology being used on the website (programing language)
- subdomains
- subdomain take over checker
- DNS records, Reverse DNS
- screenshots of sub domains
- Database being used
- Server type
- emails that belongs to the web or usernames
- hidden HTTP parameters
More:
- Tüm portswigger lab'ları ve OWASP TOP güvenlik açıkları
- Başlangıç olarak HackerOne
- Az ödül & Az rapor olan şirketler
- Yeni programlara XSS denemek
- Hesap devralma ve SQL açıkları
- Bazı şirketler rapora ip adresini eklemeni de istiyor.
Comments
No comments yet. Be the first to comment!
Leave a Comment
Comments are moderated for security reasons. Your comment will be added after review.